Requirements
Project Background and Partner Introduction
The Quantum Proximity Gateway (QPG) is a cutting-edge authentication system developed in collaboration with IBM. This system aims to revolutionise user authentication and access control by eliminating manual logins and streamlining authentication through proximity detection, facial recognition, and AI-driven profile management.
Our project sets a precedent for an innovative way to interact with LLMs via a method we named Proximity Prompting. By leveraging the proximity detection capabilities of our system, users can engage with IBM's Granite 3.2 AI model contextually and intuitively, without the friction of traditional interfaces.
Goals
- Eliminate manual logins by using BLE proximity sensing and real-time facial recognition via Raspberry Pi.
- Provide customised experiences by dynamically loading user profiles and accessibility settings.
- Enable easy settings configuration via an AI agent, implemented using Granite 3.2.
- Implement post-quantum encryption (PQC) to safeguard sensitive user data.
- Ensure zero-trust authentication by using biometric verification (facial recognition) before granting access.
- Enable role-based access control (RBAC) for shared devices.
- Establish a network of interconnected devices that communicate securely.
- Develop a modular authentication system adaptable to various industries.
- Minimise login friction in shared spaces by automatically configuring devices upon user entry.
- Improve productivity in corporate environments, education institutions, and hot-desking scenarios.
Requirements Gathering
We used a multiple approaches when collecting our requirements for the design of the QPG to ensure that our system is user-centric and industry-relevant.
- We conducted structured surveys via questionnaires* to assess the challenges with traditional authentication.
- Open and closed-ended questions were used, allowing us to gather both detailed, qualitative insights from open-ended questions while also getting quantifiable data and clear structure from closed-ended questions.
* All participants were asked to sign a research participation consent form, which outlined the details of the survey to participants and allowed them to make an informed decision on whether to participate.
Survey Data Analysis
Our user survey produced valuable insights:
The data we collected sufficiently justified the need for BLE proximity technology and facial recognition integration for auto-profile loading, as well as the implementation of an AI chatbot feature added for guidance and settings adjustments. The survey also reinforced the idea to use post-quantum encryption to enhance security.
Evaluation of Survey Methods
The survey conducted to gather user requirements was structured to identify pain points, user expectations, and feature priorities. In the future, we could refine the survey methodology further and incorporate more neutral phrasing to reduce bias and improve the survey's accuracy, allowing us to better gauge the system's real-world effectiveness.
| ✅ Strengths | ⚠️ Limitations |
|---|---|
| Direct User Insights The survey provided first-hand responses from individuals who regularly experience authentication challenges, making the data highly relevant. | Limited Sample Size The survey was conducted with a relatively small group of users, which may not be fully representative of all users. A larger dataset would be more reliable. |
| Broad Applicability The inclusion of various user groups (corporate employees, students, users with advanced accessibility requirements) ensured that diverse perspectives were captured. | Potential Response Bias Respondents may have given answers that they thought were desirable rather than their actual preferences. For example, some users might have shown support for facial recognition authentication without fully considering the privacy implications. |
| Balanced Question Design The mix of multiple-choice, closed-ended and open-ended questions allowed for both statistical analysis and deeper qualitative insights. Open-ended responses provided valuable feature suggestions, such as 2-factor authentication and an AI chatbot for editing accessibility settings. | Lack of Longitudinal Data The survey only captured a single point in time and did not account for changing user preferences over time. A user's opinion might evolve as they gain experience with new technologies or encounter real-world security breaches. |
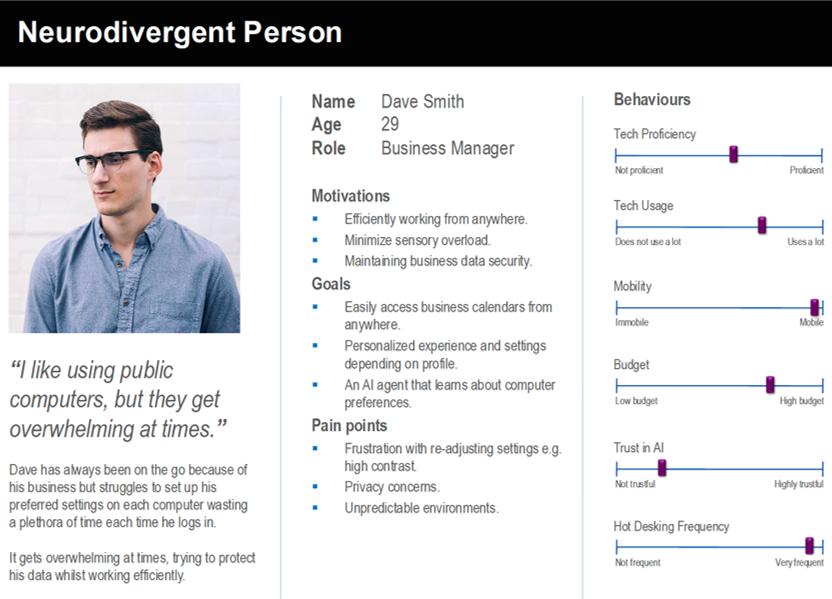
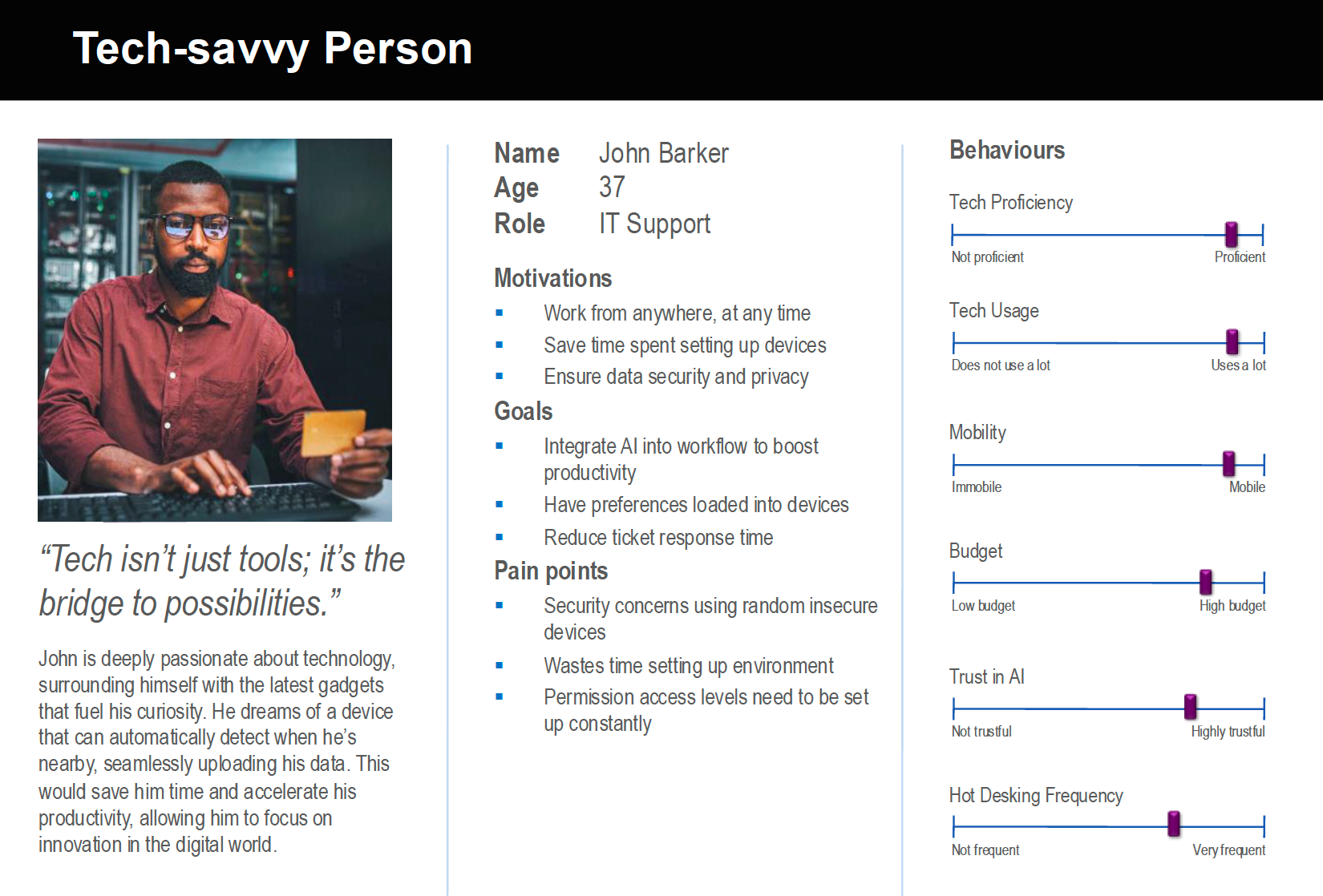
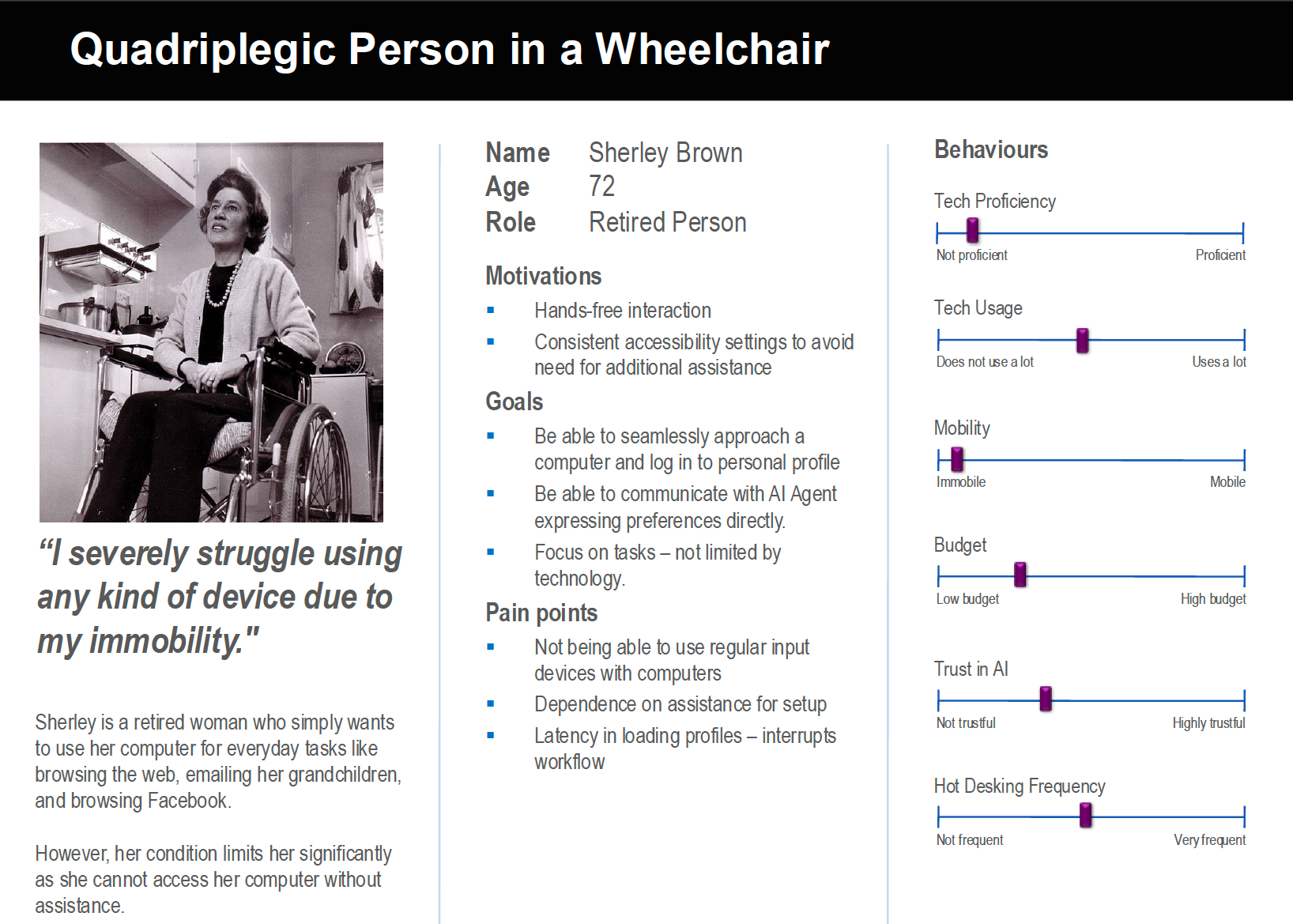
Personas
To ensure the QPG meets the needs of different user groups, we developed detailed personas representing key stakeholders and typical users of the system. These personas help in designing features that match real-world user behaviors and challenges.
From the data collected thus far from our survey and personas, we have identified these following key points prevalent throughout the data:
The surveys highlighted a need for instant, hands-free authentication without having to enter passwords repeatedly. This reinforced the necessity of Bluetooth Low Energy (BLE) proximity detection combined with real-time facial recognition to provide frictionless access to computers and shared devices.
Our survey results revealed a variety of use cases for the QPG authentication system, ranging from increasing productivity and reducing time wasted accessing devices in the office, to enhancing accessibility for users with disabilities. This diversity emphasises the importance of creating a versatile solution that adapts to a wide range of user needs and preferences.
Users appreciated the idea of AI-driven chatbot for personalising preferences. Accessibility features such as high contrast mode, larger text size, and dark mode were found to be crucial to the user experience of devices, especially to neurodivergent and elderly users, and so this feature serves a pivotal role in ensuring the QPG is user-friendly and accessible.
Use Cases
Use Case Diagram
The use case diagram below shows how users can register themselves to the system, interact with the QPG to authenticate themselves, and also use the AI Agent application.
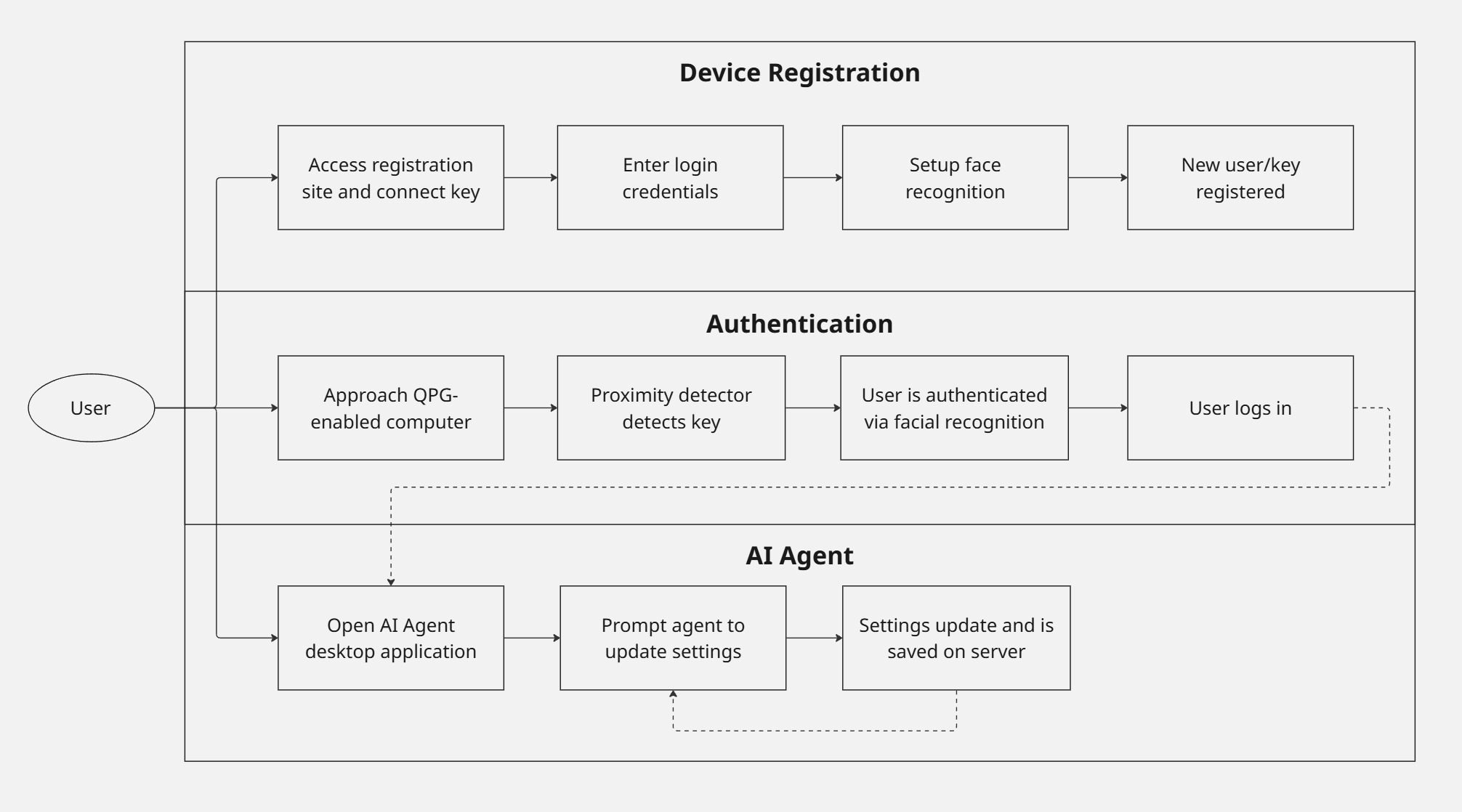
Figure 1: Use Case Diagram
Use Case List
Each use case below represents one of many potential real-world scenarios where the QPG enhances efficiency, security, and accessibility by dynamically adapting to user presence and intent.
| Actor | User e.g. Employee |
| Description | Securely log into workstation via proximity & facial recognition |
| Main flow |
|
| Result | Secure access to workstations via proximity sensiing and facial recognition |
MoSCoW Requirements List
Functional Requirements
This list defines the core features and functionalities essential for the development of the QPG. With a strong focus on seamless authentication, secure accessibility, and adaptive user control, the QPG leverages BLE proximity detection, facial recognition, post-quantum encryption and AI-driven profile management to provide a frictionless login experience. While the primary focus remains on robust security and usability, the system also considers potential enhancements such as advanced directional proximity detection, and intelligent device-switching capabilities.
Non-Functional Requirements
Non-functional requirements define the quality attributes, constraints, and operational characteristics of the QPG. Our project is strongly focused on accessibility, designed to facilitate easier device access for neurodivergent and disabled users. As such, the non-functional requirements that we prioritised include reliability, performance, and usability, ensuring that all users can have easy access to their devices regardless of their physical or technical abilities.